A Great Week: Edition 5

Cyber Security has been a hot topic for the past few years.
It will be discussed furthermore in the coming days with the increasing cyberattacks. I always thought how cool it would be to predict the likelihood of an event? I used that lens to understand what helps ascertain the likelihood of cyber security incidents.
You will understand the factors influencing the likelihood of a cyber security incident but about a more suitable metric. Read on.
Most of the cyber security stats play to the innate fears of people.
Everyone talks about the sky falling. Every statistic amplifies it.
Here are some examples:
- There is an estimated cyber attack every 39 seconds. (University of Maryland)
- Cyber Crimes have increased 600% due to covid 19
- macOS malware up by 165% in 2021
- Ransomware attacks have risen by 350% and are estimated to cost $6Trillion in 2021
- The average cost of a data breach is $8.19 Million/breach.
These stats scare the executives who worry for their business. 🤯. These stats help consulting companies sell better. 🤑
While it is not a fluke that cyber attacks have increased manifolds and even state-sponsored attacks have gone up in numbers, where is the balance?
How should an executive responsible for cyber security take action?
Identifying vulnerabilities in the systems
Focusing on vulnerabilities was a common approach for years. It gives a good idea of gaping holes in enterprises. Engineering teams go into customer ecosystems and study and compare to the best practices and frameworks(NIST), policies, patches, and guidelines. It is highly comparative with a certain baseline suitable for an organization and maturity levels. There are several tools to scan and identify vulnerabilities across network, cloud, data, Identity, and access management. Typically in these reports, the engineers can also guide how severe these gaps are. As you will see, the approach is not very effective in itself.

Understanding the likelihood of cyber security events
Security professionals have gone after identifying the likelihood for a while. Modern risk modeling takes that into account. But the truth remains, predicting likelihood is a really hard task. Models can be heavily skewed to the quality of data. Moreover, there is significant training and feedback loop required to train the models for accurate predictions. then there are external factors like intelligence from security providers, trends in the market or industries, geolocation data, certain patterns of exploitation, etc. an accurate likelihood prediction must take those into account and spit out something used.
so, while it is a cool metric to chase down, it is a complex task to be able to get into prediction.
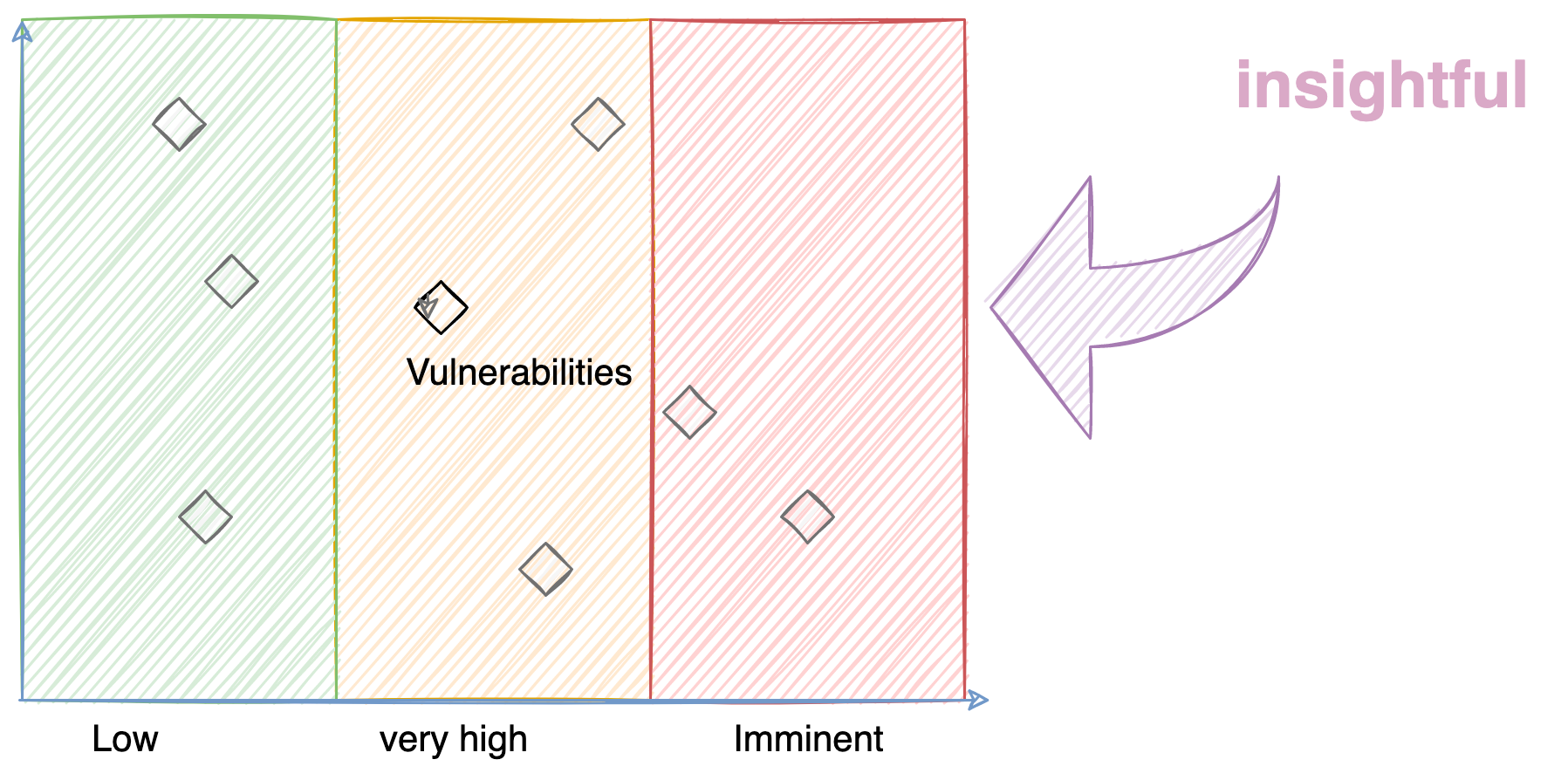
A Rather better metric - Impact
How would you feel if we tagged an event with very high likelihood but no or Minimal business impact?
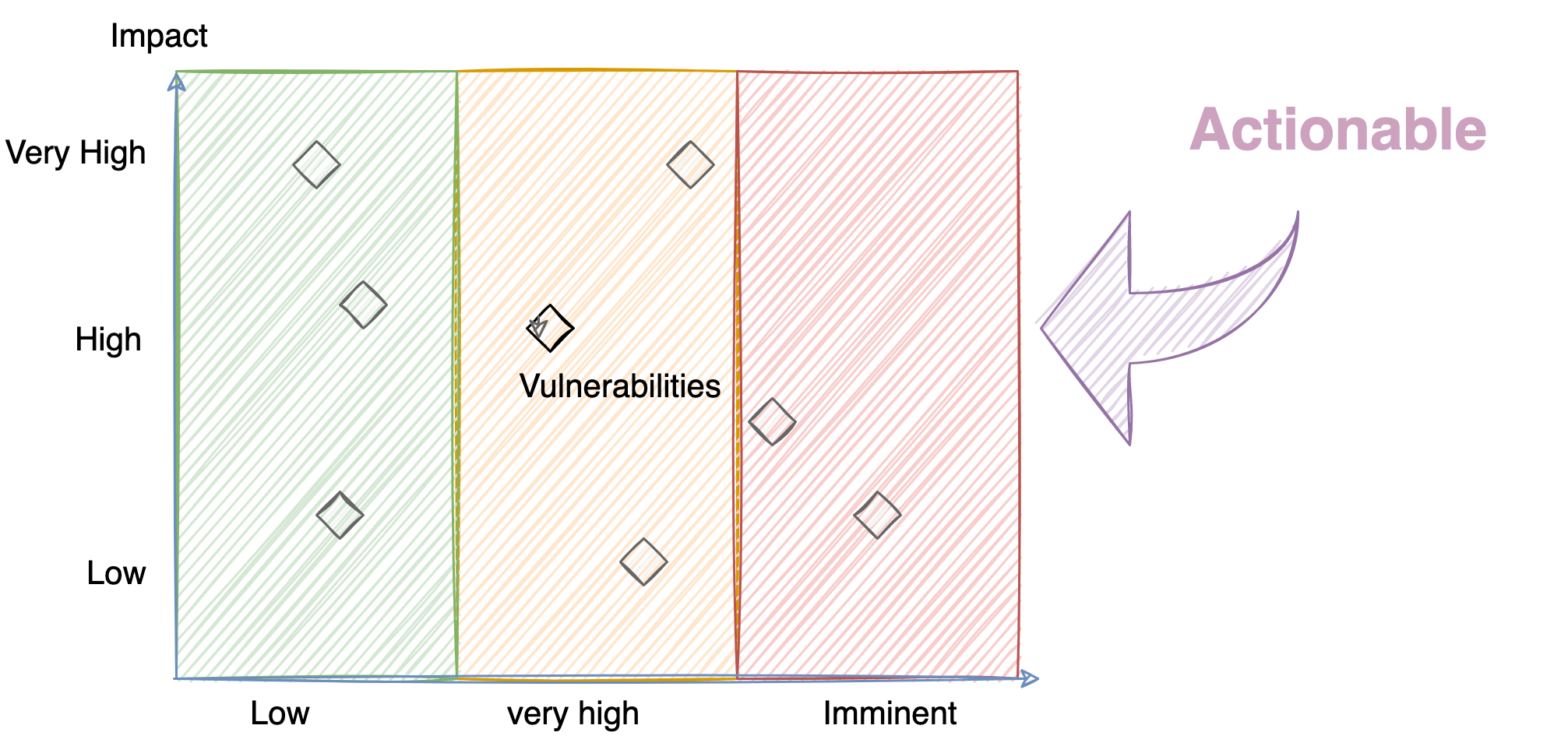
It changes the whole scenario. Isn't it?
The outcome or the impact is far more superior and actionable metric.
Rather than being afraid of the statistics, it is far more helpful to contextualize threats and vulnerabilities for your business.
Furthermore, a business can draw worst-case scenarios and conduct exercises to see their level of preparation in dealing with those scenarios.
It forces you to consider:
- What is the impact on our business of this scenario playing out in real life?
- Is there a financial risk with this scenario?
- Is there is a business disruption?
- Is there an impact on our shareholder value? Our partners
- How do we recover?
- How soon can we recover?
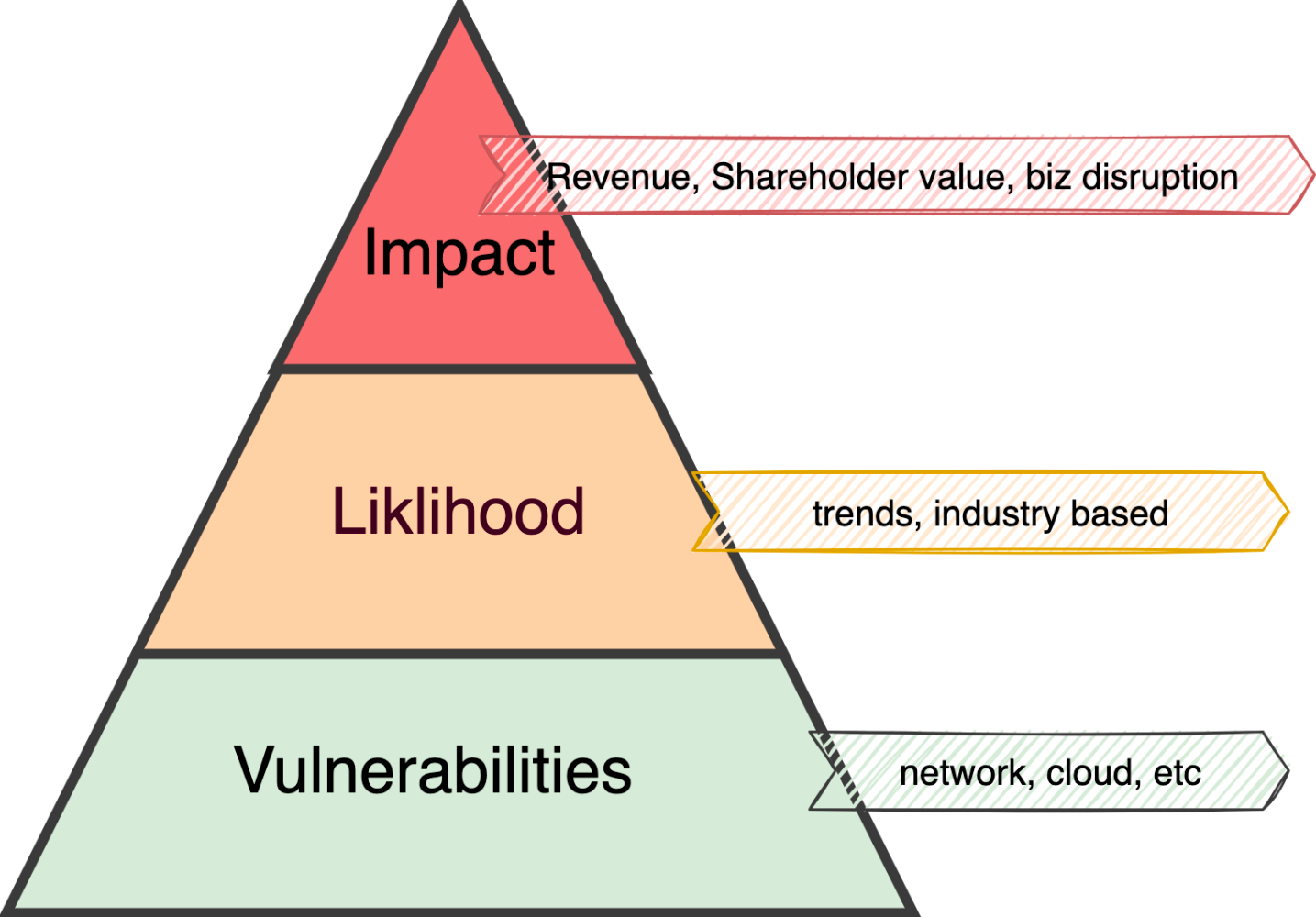
When you connect vulnerabilities, likelihood, and impact, the activity becomes actionable and measurable. A better picture emerges.
It forces you to focus on the top priority items.
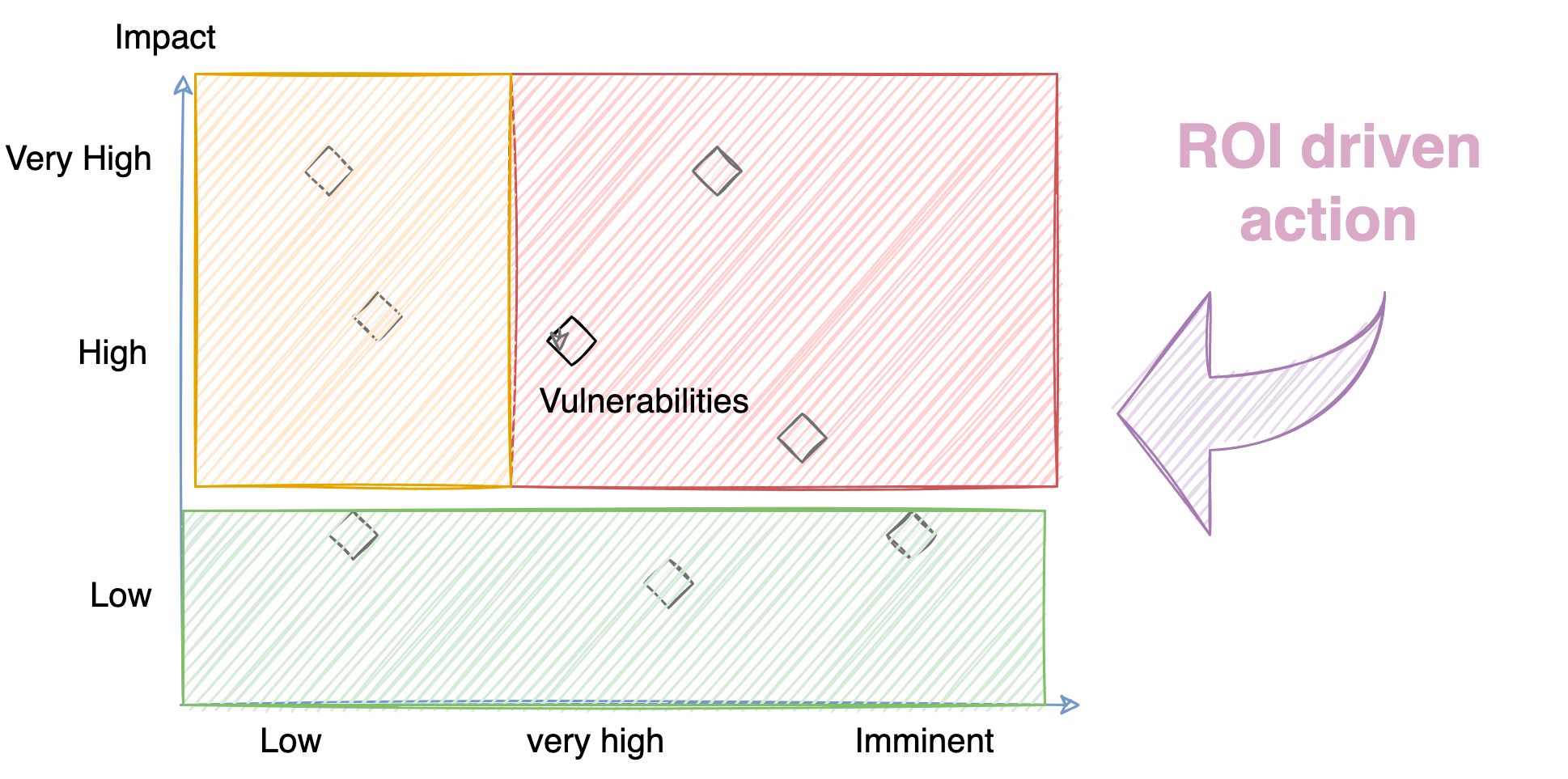
Order of Priorities for taking action
Priority 1: Very high or High Impact Items with Imminent or high degree of likelihood
Priority 2: Very high or High Impact items with medium to low degree of likelihood
Priority 3: Low Impact items with imminent, Very high, or Low degree of likelihood
The senior leadership can tie investments to these actions and priorities.
Parting thoughts
Enterprises should focus on business impact and not just vulnerabilities and threats. Enterprises must use assumed likelihood to draw worst-case scenarios and prioritized by business impact. Instead of focusing on the negative sentiment in the broader market, it is valuable to contextualize these threats and ensure they can build resilience in their business by preparing for the worst-case scenarios.