E10: These 5 Collaboration approaches Can Help You Strengthen Cyber Security
Security leaders run their teams and operations from the front of any organization.
Security is the key and is central to any enterprise business strategy.
However, there are unique issues to address as Security teams pivot to open culture and enable innovation.
- The Core security team is relatively small
- Security teams cant cater to the entire organization in the old-fashioned ways.
- The pace of change is faster than ever before.
- Threats are more sophisticated than ever before.
- Security leaders can not be part of every strategic and tactical decision.
I submit -collaboration will drive the future of enterprise security.
A decentralized model with shared responsibility will be the future.
Security leaders will join hands with BU heads who will become security torchbearers in their areas.

Where are the challenges?
Some data points:
- You are just a credit card and a free trial away from trying a new tool on the internet.
- Organizations want to provide a self-serve environment of experimentation to team members. Applications, tools, data are being experimented with at an unprecedented rate.
- An enterprise with a complete set of security tools(detect, triage, analyze) takes an average of 8 days to complete a Security Investigation.
- An average of 6 to 15 tools are used for incident resolution.
- Threats are mounting at an unprecedented rate.
- Collaboration is the #2 or #3 item on any survey of what security pros are looking for, behind Investments in detection and prevention tools.
What is collaboration important?
Complexity and elapsed time challenge
The complete cycle from prevention -> detection -> triage -> analysis -> containment -> remediation can be tedious and needs a lot of work across tools and skillset.
At any given time, 8- 10 different roles may be involved with some degree of overlap in the prevention to remediation cycle.
- Security Architects
- SOC analysts
- Security engineers
- Incident responders
- CISO/Security chief
- Endpoint administrators
- Corporate departments and teams from the impacted application.

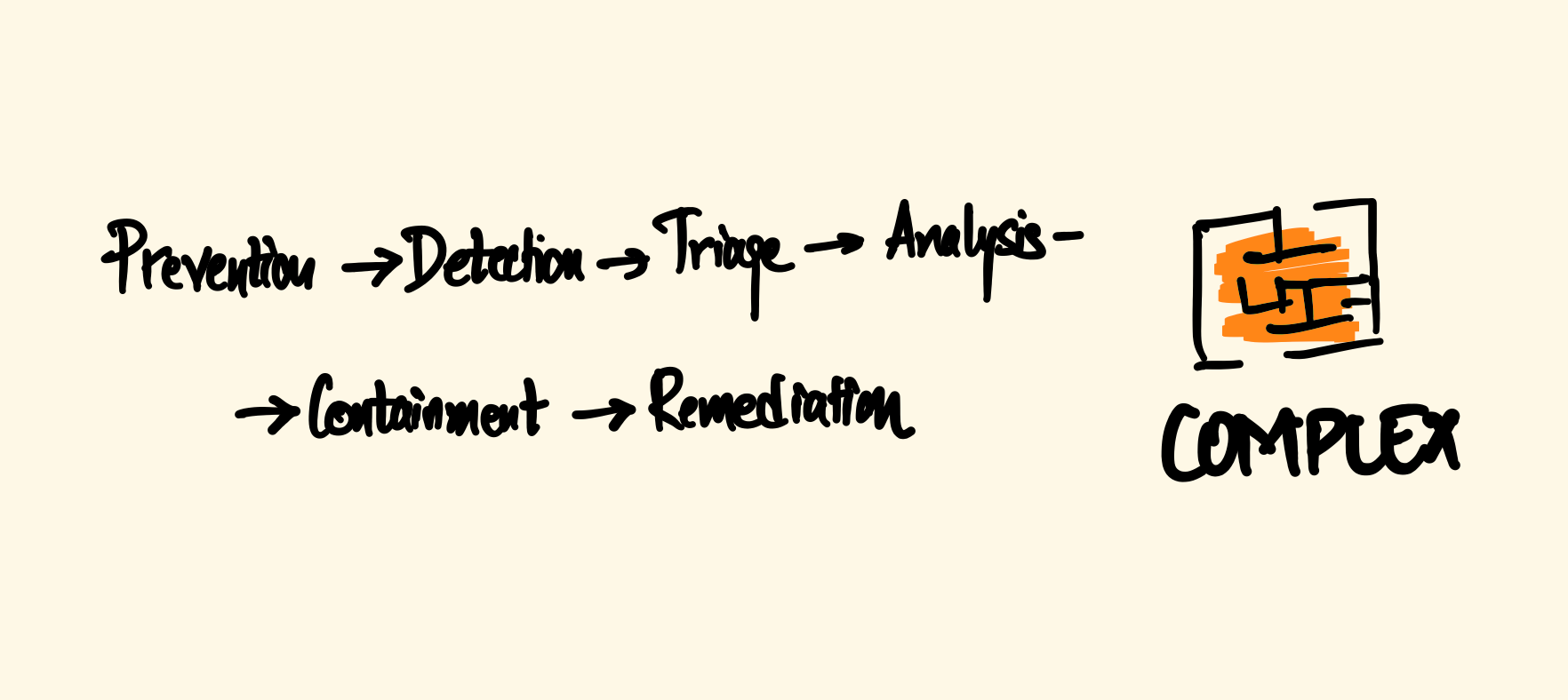
Problem of Scale
It is not humanly possible for the security team to be part of every strategic and tactical decision around architecture, applications & data. hence,
So the decentralized model of security will essentially depend on cyber security teams leading with the key processes, controls, tools, methods that keep the organization safe and make them resilient and hands-on of those practices, processes, and best practices to these collaborators across the organization at various levels.

#1 approach to establishing collaboration
Creating an organizational model for security is the way to go. An organizational security collaboration can be split at three levels within the organization:
- Core strategy, Decisions, Frameworks, Compliance, Automation, Audits are Managed and laid by the CISO office. Consider it it central hub.
- Application or BU level decisions, architecture are Managed jointly among the technical teams and intertwined security engineers. this enables them to set guard rails around sensitive data, applications, services, IAM, and specific roles which would be required.
- Granular scenarios within the perimeters of the guard rails are led by champions/collaborators within those BUs. Any exceptions here should still be caught by the automation toolset.

Other means to enable collaboration
#2: Centralized environment -> Access, assess, and act by role.
#3: Information sharing among various teams on a real-time basis
#4: Levels of trust among the teams
#5: Going away from typing information, manually feeding across various systems and teams leads to errors. Automation is the key
In the end
The collaboration will contribute to real-time visibility—connecting people, processes, and technology across events, data, and systems. Those who are setting up the means to collaborate- automation, centralized environments, information sharing, and Trust are already seeing benefits of collaboration in business velocity increase.
What has been your experience?